I received a notification last night that someone changed my shipping address on Macys.com and when I visited the website, there was an open order for a PS5 with delivery to:
DONT IEPN 203 W PITTSBURGH AVE WILDWOOD CREST NJ 08260
After logging into Macy’s I got 43 emails at once to seven different services like “Excalidraw” and “Sportograf” trying to login using a magic link.
At this point was was pretty nervous so I checked my main email security. Sure enough, there have been repeated login attempts under my account going on every few minutes for weeks.
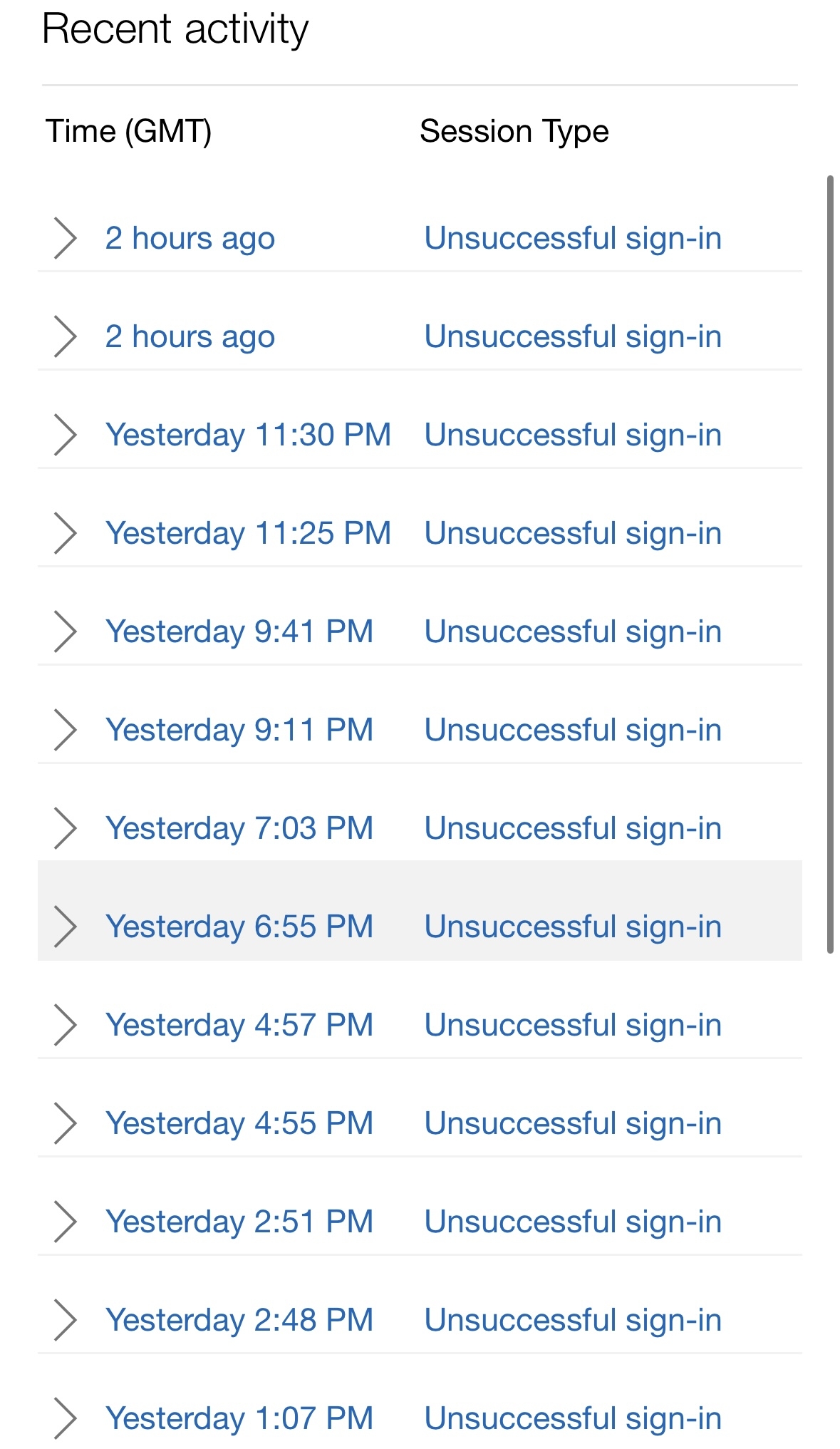
I also saw there was an attempted login to my cellphone or home internet company.
I use 2FA, authenticators, etc. Basically what else should I be doing? Is there any way to be more preventative? I really don’t wanna chuck this email but it is possible that may be the safest recourse. I do use this email for almost 300 different accounts to various things though.
you can use a service like SimpleLogin.io to generate email aliases for each site. you get 10 free
ever since I’ve started using it not asingle website has gotten my bare email
Your username and password common probably leaked from somewhere. It happens when services you use have a breach.
This is why it is recommended to not use the same password for everything, as well as changing your password once in a while.
Also, I recommend putting your email into https://haveibeenpwned.com/ and it will let you know if your address has been part of any breaches that it is aware of. Optional: Sign up, and you’ll be emailed if your address does appear at a later date.
Technical advice has been given already, but also consider reporting the fraudulent order to Macy’s and the police if not done yet.
and when I visited the website, there was an open order for a PS5 with delivery to:
After logging into Macy’s I got 43 emails at once to seven different services
Did you manually navigate to Macys.com, or did you click a link in the email to “Macys.com”? Because it’s a common phishing technique, they may have used your macys email and password to password spray every other website they could find it associated with when you “logged in.” It’s usually a page that’s spoofed to look like a legitimate login page, which redirects you to the actual page once it records a login attempt.
Also check HaveIBeenPwned.com, your email may show up in a few major beaches, which is enough for script kiddies to spray it across the entire net.
Dude, that’s some next-level nightmare fuel. So, your email’s getting hit harder than me on a weekend bender, and now some joker’s ordering a PS5 to a sketchy address? Sounds like a bad trip. First off, lock everything down tighter than a bottle of cheap vodka—I’m talking changing passwords, upping that 2FA game, and maybe even looking into a password manager if you haven’t already.
But honestly, if they’ve been poking around in your email like it’s a free-for-all, you might need to nuke that thing from orbit. I know it sucks to think about, especially with all those accounts tied to it, but it’s better than letting some cyber junkie run wild with your info. Maybe set up a new email for the important stuff, keep it under wraps like your last stash, and slowly start moving things over. And for the love of whatever, stay on top of your security game—ain’t nothing worse than waking up to a digital hangover that costs you more than your last bender.
Change email password just to be on the safe side. Make sure no device connected to your local internet is compromised. Give a Malwarebytes scan to your PC and look up your IoT devices (if you have any) to see if they had any history of vulnerabilities.
Do NOT use same passwords on multiple sites, or at the very least, salt your password based on the site. (add characters based on what site you’re visiting). For maximum security, use a password manager like KeePass.
Do NOT use a similar password to your very crucial passwords (your email, goverment sites etc.) anywhere no matter what.
Inform macys about your account being compromised; if your credit card was charged; issue a chargeback.
Pretty common practice with leaked login info. Also generally they’ll email bomb you after ordering to try to hide the order email. They’ll even try hitting every site imaginable with the same combo. This is why I love “hide my email” with Apple. Different generated emails and passwords for everything with a tap.
Change your macys account to a different email.
You can change your password to be sure, but there’s nothing you can do to prevent the attacker from entering your email address into the login field of your mail service.
Be extra watchful for phishing attempts. If you’re using TOTP or SMS for authentication, consider using Passkeys or a Yubikey(-like device), as TOTP and SMS codes are easily phished.
Changing your password on your Macy’s account and any other account that may share a password should be a priority, if you haven’t already. Other than that, not much you can do but hope the annoyance goes over quickly.
If you don’t use Macys, consider deleting your account there or changing your email connected to it.
If you use a strong password and 2fa, there’s no way to prevent login attempts, and a strong enough authentication will make random login attempts just a nuicance. You can set up a recovery address (that must be equally safe). If you are using an online password manager, check there was no known leak
There is 1 way to stop login attempts. Use an alias provider (e.g. simplelogin.io), and change the account emails to a randomly generated alias.
Even if you used the same password everywhere, as long as the email/username for the account is randomly generated the password is essentially useless.
Or plus addressed email aliases, which are free. Most automated spamming software do not remove the plus so you can block most of them like that. I use them.
There are free services that allow you to create countless emails, one per site is ideal, just like one (different) password per site. Addy and Simplelogin have a generous free tier, last I checked the first one allows for unlimited receive-only addresses (when shopping it’s very rare you need to respond), the second gives you some two-way addresses.
If you get a domain, many registrars include free mail service, and have mail forwarding, or “redirecting”, which basically will allow you to create countless addresses (that can also send/respond) for your one account (You add these “email forwards”, or “Identities”, to your app of choice, like K9-Mail for android). You don’t necessarily need to buy their separate email package (although the interface might be more convenient). I’ll give you one example which includes email: OVHcloud, one of the largest clouds in europe.
If you can afford it there are all-in-one services like Soverin with easier interface.
It might be wise to start a slow process of migrating (or maybe deleting and creating again) accounts, and saving all this stuff in a password manager (like KeepassXC) if you aren’t already.
I use 2FA, authenticators, etc.
If this is the case, how did you not know these login attempts were happening? Shouldn’t you get a ping when a login is attempted and can decline it if it’s unauthorized?
If you use something like Aegis (which works offline) you just decrypt your database every time you want to log in and copy the 2FA code from the app. It doesn’t ping you because it generates codes offline, i.e. it’s not connected to whatever service you’re using 2FA with.
Only if they already have the correct password.
I viewed the recent activity in my account. I did not receive any notifications of failed logins in the last 8 weeks its been going on. I assume because I use 2FA and the password is just wrong it doesn’t bother cause of the frequency it happens.
You are correct, my bad. Seems like you can have some confidence that your email is secure, at least








