It’s a bad title, but I’m trying to figure out how to describe what I want.
First, I got my photoprism working thru cloudflare. Now, on the same domain I would like an email address.
So mysite.com gets routed to 56.654.234.12 let’s say by cloudflare such that a global user never sees my ip. But mail.mysite.com that’s different, they don’t proxy email so if you do a reverse lookup you can find the origin IP.
I heard about tunnels so I stupidly signed up for that, only to learn that a tunnel just lets you into an internal network. So an SMTP server can’t get emails from outside that way.
Ideally, somehow I could setup one user at Gmail or proton mail, then somehow setup the same or different user...user1@mysite.com and I could then use mailu, mailcow, mail docker to house my user1@mysite.com which routes mail thru Gmail or protonmail. I know all this makes little sense because I don’t know the proper way, so that’s my question for you smart people who have done this twice over. Could someone point me to the best way of setting up a local mail server that routes thru cloudflare but is not easily reverse looked up? Is that even a problem at all?
In the end, I want to have my emails self hosted from my house. Meaning that I can go to my local computers or my phone locally or remotely to the mailu interface, I can send and receive emails using my user1@mysite.com email and none of that email ends up on a Gmail or protonmail server stuck there forever. I can’t download all my Gmail to Thunderbird on my computer because then my phone would not have access to it. So to me that just means that I need to host the email server at home, but how to safely access it is the ideal solution.
Avoiding spam filters and ISP blocks are a common issue with self hosted email.
Ideally you’ll have a mature domain, dkim configured and an IP that’s not blacklisted on a network that allows email traffic.
OVH offers pretty cheap email hosting if you just want a turn key solution.
Otherwise if you want your home lab to work this way you may need to configure something akin to a forward proxy on a VPS to act as a gateway for your homelab.
This could be achieved using wireguard and iptables. By routing the email traffic to your homelab.
maybe a vpn provider that uses openvpn? advanced setup but you can have an openvpn client auto connect on boot and bind the mail and ddclient to the tunnel interface.
cloudflare has good support for ddclient, so when your IP changes updates are automatic.
Not how that works.
what about that doesn’t work? just because you don’t know how doesn’t mean not possible.
https://developers.cloudflare.com/dns/manage-dns-records/how-to/managing-dynamic-ip-addresses/
https://github.com/ddclient/ddclient#using-ddclient-with-dhcpcd
https://openvpn.net/community-resources/configuring-openvpn-to-run-automatically-on-system-startup/
Jake, the OP is asking for something that actually works. You’re just throwing out some random bits that says you get two ports to talk to each other, but like I said…that’s not how this works. You can read my other post in the thread if you want, or go read about actually hosting SMTP service out in the world, and the nightmare it is.
Mail hosting is not that simple anymore. Your understanding of how it works is missing an entire world of complex issues that you need to solve outside of just hosting a mail server with an open SMTP port.
The biggest certainty is that just having an open port for an SMTP server dangling out there means you will 100% be attacked. Not just sometimes, non-stop. So you don’t want to host on a machine with anything else on it, cuz security. So you need a dedicated host for that portion, and a very capable and restrictive intrusion detection system (let’s say crowdsec), which is going to take some amount of resources to run, and stop your machine from toppling over.
Next, you need all your secondary record systems (SPF, DKIM, DMARC) pointing at a defined and unchanging record for your SMTP server, so you’ll need a static IP. If you don’t have that already, you’re kind of SOL.
Next, you’ll need to be running your own peer authentication system, then a spam filtering system (of which none of them work well without massive amounts of sample data, but you can use public lists to help block known bad actors), decent file threat scanning…you see where I’m going with this. It all takes a fair amount of resources, and even more if/when you get bad actors spamming the machine all the time.
Finally, you’ll probably want this machine completely segmented from the rest of your network, which isn’t really complicated, just costs a bit more money.
There’s a reason why mail hosts and forwarding services cost money, and still exist. It takes a large amount of effort to be somewhat secure, or at least to best of your efforts. With the added costs associated with hosting your own mail servers, most people just avoid the hell out of it. I certainly wouldn’t recommend it.
I hear you. However I’m a practical person. I understand that spam has made it difficult for everyone to use email. How can I put this. Basically I got a ton of emails trapped in Google servers. I like the idea that someone proposed of using paperless since I already use that. But also I guess email is worthless so I shouldn’t keep trying? Maybe you’re right. It’s time for email to not be used. Any suggestions for what I should use instead of email which are a few clicks and done?
It’s an easy fix, if I and everyone else can’t setup our own servers safely, then why use email at all? Just stop using email and let Gmail add a few thousand more hoops…portggf, sspf, dkjg, Chddth, Chat-GPT. Whatever they want so it is super super “safe”. The rest of us, are we stupid? What about this message? How come this is easy? Setup my own instance and bam I can talk to other people with very little spam I literally have to work to get any attention at all on the fediverse. Why isn’t there a file/text sending app for the fediverse yet? Or maybe there’s one and I just haven’t seen it yet?
The biggest certainty is that just having an open port for an SMTP server dangling out there means you will 100% be attacked. Not just sometimes, non-stop. So you don’t want to host on a machine with anything else on it, cuz security. So you need a dedicated host for that portion, and a very capable and restrictive intrusion detection system (let’s say crowdsec), which is going to take some amount of resources to run, and stop your machine from toppling over.
I need to call BS on this. No one cares. I’ve been running a small go-smtp based server that would do some processing on forwarded mail for 2 years now and I don’t see much of “attacks”. Yeah, sometimes I get passersbys trying to figure if this is a mail relay, which it’s not.
You absolutely don’t need a dedicated machine and an IDS. And you definitely need crowdsec.
Yeah, sending mail is somewhat hard lately, but DKIM and DMARC can be figured out. Receiving mail is just straightforward.
As is your want to do. I’ve run thousands of different combinations and type of SMTP related services at all stages of processing, and I’ve seen the above 100% of the time.
You are talking about receiving mail from another forwarded entity. It’s not the same thing. You’re also proving my point, because you’re already getting your intake handled upstream, so there you go. What I said is accurate. 👍
I won’t quote the bit of your post again, but no, if you have an open smtp port then you won’t get constantly attacked. Again, I have a fully qualified smtp server and it receives about 40 connections per hour (mostly the spam ones). That’s trivial to process.
It doesn’t matter that I forward emails from another server, because, in the end, mine is still public on the internet.
If you are trying to make a point that it’s tricky to run a corporate-scale smtp and make sure that end users are protected, then it’s clearly not what the OP was looking for.
Super cool story though.
The biggest certainty is that just having an open port for an SMTP server dangling out there means you will 100% be attacked.
True.
Not just sometimes, non-stop.
True
So you don’t want to host on a machine with anything else on it, cuz security.
I don’t think “cuz security” is a proper argument or no one would be ever listening on public internet. Are there risks? Yes.
So you need a dedicated host for that portion
Bullshit. You do not need a dedicated host for smtp ingress. It won’t be attacked that much.
and a very capable and restrictive intrusion detection system (let’s say crowdsec), which is going to take some amount of resources to run, and stop your machine from toppling over.
That’s not part of the mail pipeline the OP asked for.
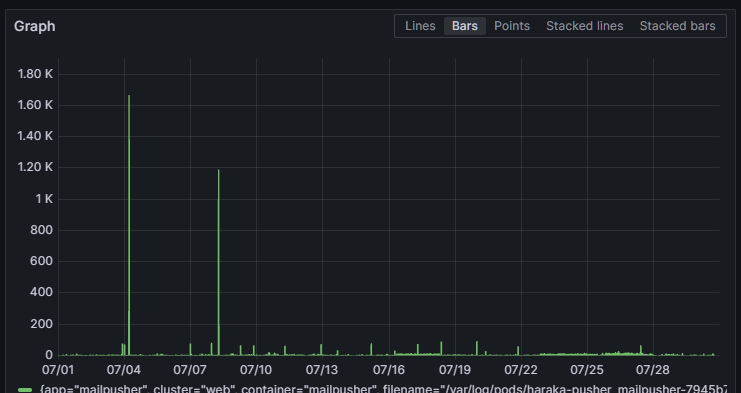
Here, I brought receipts. There are two spikes of attempted connections in the last month, but it’s all negligible traffic.
Self-hosting mail servers is tricky, same as self-hosting ssh, http, or whatever else. But it’s totally doable even on an aging RPi. No, you don’t need to train expensive spam detection because it’s enough to have very strict rules on where you get mail from and drop 99% of the traffic because it will be compliant. No, you don’t need to run crowdstrike for a server that accepts bytes and stores them for another server (IMAP) to offer them to you. You don’t even need an antivirus, it’s not part of mail hosting, really.
Instead of bickering and posturing, you could have spent your time better educating OP on the best practices, e.g. like this.
I’ve found some interesting options here, but everyone wants to own your data. Just put it all in our servers, c’mon! It’s free or low price, we’re you centric and not as centric…
Sure. But I want my stuff in my basement server and not in their basement server 😭.
You can just route your outgoing emails through a relay server. I‘ve hosted my own mail server with outgoing traffic going through aws simple email service for over a year now without any problems. You give some data to amazon but only outgoing mails and it is pretty cheap, like 10 cents per month.
Here’s a good example of why I’m getting out of Gmail:
https://portswigger.net/daily-swig/encrypted-email-service-ctemplar-announces-closure
Since the government already has their sights on breaking them up, it would be a good idea to GTFO way before they implode:
Acronyms, initialisms, abbreviations, contractions, and other phrases which expand to something larger, that I’ve seen in this thread:
Fewer Letters More Letters DNS Domain Name Service/System IP Internet Protocol SMTP Simple Mail Transfer Protocol VPS Virtual Private Server (opposed to shared hosting)
[Thread #924 for this sub, first seen 18th Aug 2024, 19:55] [FAQ] [Full list] [Contact] [Source code]
Have a look at https://forwardemail.net/. It’s a service that handles accepting (and optionally sending) email on your domain, and forwarding any received mail to other backend services, like a gmail account. All you need to do is set some DNS records, like MX and their servers will handle everything. It works fine with domains hosted on cloudflare, and has excellent howto’s to get everything set up and running.
Edit: The great thing about this service, imho, is their guides. They don’t just have a static howto, they template in your information into the exact string you need to copy/paste into the service provider’s web interface. Want to encrypt your plaintext TXT records? There’s a button for that on the guide. Want to learn how to get around a port 25 ISP block, they have a guide for that. Want to set up proper Send-As from Gmail using their SMTP server? There’s a guide for that. :-)
Looks good but it’s basically another place for my emails to be be stuck at for decades. Maybe I’ll look at the way they route email.
It might be worth taking a step back and looking at your objective with all of this and why you are doing it in the first place.
If it’s for privacy, then unfortunately that ship has sailed when it comes to email. It’s the digital equivalent of a post card. It’s inherently not private. Nothing you do will make it private. Even services like proton Mail aren’t private–unless you only email other people on proton.
I appreciate wanting to control your own destiny with it but there are much more productive things you could be spending your time on the improve your privacy surface area.



